WordPress Access Logs play a vital role in the management and optimization of a WordPress website by serving as a detailed record of all interactions and activities taking place on a site. Essentially, these logs capture and store data about every access request made to a website, providing a comprehensive audit trail of user activity. For web administrators and developers, access logs are indispensable tools, offering insights into traffic patterns and user behavior, which are crucial for both security and performance optimization.
At their core, WordPress access logs are records that log each request made to a server, detailing information such as the IP address of the requester, the requested URL, date and time of access, and the status of the response delivered. Within a WordPress environment, access logs are instrumental in monitoring site activity, enabling webmasters to track interactions, identify errors, and ensure the seamless operation of the site.
These logs are particularly important for enhancing website security. By analyzing access log data, administrators can detect unauthorized access attempts, identify potential security breaches, and implement measures to deter future threats. The logging system aids in the detection of anomalies, such as unusual login attempts or specific patterns indicative of malicious behavior, thus acting as a frontline defense mechanism against cyber threats.
Beyond security, WordPress access logs significantly contribute to performance monitoring and optimization. By examining traffic data, developers can identify peak times of usage, assess the effectiveness of marketing campaigns, and pinpoint areas where the site may be experiencing slowdowns or errors. This real-time data enables proactive management, helping to troubleshoot performance issues before they escalate into more significant problems.
In the broader context of WordPress site development, access logs provide a foundation for informed decision-making. The data gathered helps not only in maintaining the operational integrity of a website but also in enhancing its overall user experience and accessibility. Through careful log analysis, developers can make data-driven adjustments to optimize content distribution and improve load times, ensuring that the site remains responsive and user-friendly.
Ultimately, WordPress access logs are an essential component of a robust website management strategy, offering a continuous feed of valuable insights that support the ongoing improvement of site performance, security, and user engagement.
Log Structure
In the realm of WordPress website development, understanding the structure of access logs is pivotal to optimizing performance and maintaining security. Access logs serve as a detailed record of every request made to the server, capturing valuable data about how users interact with a WordPress site. These logs are instrumental in organizing and managing data effectively, enabling seamless tracking and monitoring of activities.
At the core, the log structure within WordPress environments is designed to organize vast amounts of information efficiently. This structure includes critical components such as IP addresses, timestamps, request methods, and response codes, each playing a significant role in ensuring data is meticulously recorded and easily retrievable. By having a defined structure, access logs help in diagnosing issues, enhancing performance, and fortifying security measures such as identifying potential threats and abnormal activities.
A well-organized log structure facilitates the extraction of performance insights. By systematically tracking user activities and server responses, developers can pinpoint bottlenecks and optimize load times, which is crucial for improving user experience. Furthermore, the logs’ structured data provides a clear view of resource access patterns, aiding in effective resource allocation and management.
In terms of security applications, access logs serve as a primary source for recognizing unauthorized access attempts. The ability to analyze logs enables administrators to detect and respond swiftly to security breaches. The structured format aids in correlating suspicious activities and applying preventive measures, thereby safeguarding the WordPress site from potential threats.
The structured nature of WordPress access logs not only supports robust data organization but also ensures seamless integration with analytics and diagnostics tools. This integration empowers developers and site administrators with actionable insights, allowing for proactive management and optimization. In essence, the log structure is an indispensable asset for ensuring the WordPress website operates smoothly, securely, and efficiently.
IP Address
An IP address, short for Internet Protocol address, functions as a unique identifier assigned to each device connected to a network. It serves a crucial role in facilitating communication between devices by ensuring data packets are sent to the correct destination. In the realm of WordPress websites, IP addresses gain significance for tracking and analyzing user activity. They become indispensable in accessing the logs that detail every visit to a WordPress site. Understanding these logs helps developers monitor user interactions, optimize website performance, and maintain security protocols.
IP addresses are categorized into two main types: IPv4 and IPv6. IPv4 addresses consist of a sequence of four numbers separated by periods, while IPv6 addresses are longer, using alphanumeric characters separated by colons. These IP addresses not only identify individual users but also highlight geographic locations, providing insights into user demographics and behavior patterns.
Within the WordPress setting, analyzing IP addresses aids in the detection of unauthorized access attempts, flags potential security threats, and helps implement measures to protect sensitive data. By monitoring IP addresses, developers can trace suspicious activities and devise strategies to mitigate risks, thereby enhancing the security framework of the website.
Furthermore, IP analysis is instrumental in managing network traffic. Understanding the origin of traffic through IP addresses allows developers to allocate resources more efficiently and tailor content to suit the audience’s preferences. This monitoring extends to optimizing the overall user experience by ensuring a seamless and responsive website environment.
Using IP address data effectively involves deploying various best practices. Regularly updating and reviewing access logs, combining IP analytics with other user behavior metrics, and employing automated tools to flag anomalies are pivotal in leveraging these identifiers. Collectively, these efforts not only bolster the security of a WordPress site but also enhance its performance by delivering a more personalized and secure experience to its users.
Timestamp
In the dynamic environment of WordPress Access Logs, timestamps play an indispensable role. They serve as a cornerstone by capturing the exact moments when actions occur on a website. In the context of managing a WordPress site, timestamps encapsulate the sequence of visits and activities, providing vital data for understanding how users interact with the site.
By storing these moments, timestamps allow site administrators to observe patterns in site access, revealing when the traffic peaks or lulls. This understanding is crucial for resource allocation and ensuring the site performs optimally during high-traffic periods. Site managers can thus monitor visitor behavior with precision, enhancing the overall management process by facilitating timely interventions and adjustments.
Moreover, timestamps contribute significantly to website security. By meticulously recording access times, they assist in identifying unusual access patterns that might suggest security breaches. Spotting these patterns early allows for quick responses to potential threats, ensuring the site’s integrity remains intact.
As timestamps are inherently tied to access logs, they provide a timeline of visitor interactions which, when analyzed, can reveal insights into site efficacy. This chronological data empowers site managers to make informed decisions that enhance both user satisfaction and site performance.
Conclusively, timestamps in WordPress Access Logs are much more than mere indicators of time—they are vital tools that enhance site management by offering clarity and insights into user interactions. This knowledge supports not only the optimization of the site’s operational framework but also reinforces its security posture, leading to an improved and more reliable user experience.
Request Type
WordPress access logs serve as a fundamental tool in the landscape of website management. They are vital to understanding how different request types interact within a WordPress environment, providing a window into the activity that occurs on the website. These logs capture data about every request made to the server, including details about user interactions and system processes.
The types of requests associated with WordPress access logs encompass several categories, each contributing to the broader goal of effective site management. Primarily, there is the distinction between HTTP methods — GET and POST requests are the most common. GET requests are used to retrieve data from the server, typically needed to load pages or resources, while POST requests are used to send data to the server, often for forms or updates. These methods ensure that data flow to and from the WordPress site is efficient and traceable.
Another critical request type stems from security-focused operations, such as tracking unsuccessful login attempts. Monitoring these kinds of requests is crucial for identifying potential security threats. Admin requests also form an important part of access logs, encompassing actions taken by site administrators relating to changes in website settings or content management processes.
Request monitoring helps in understanding user interactions, analyzing traffic patterns, and detecting anomalies. Through access log analysis, administrators gain insights into page performance metrics and server response times, essential for optimizing a WordPress website’s efficiency and user experience. Moreover, by applying techniques of request analysis, potential vulnerabilities can be identified, thereby enhancing the site’s security posture.
Access logs thereby integrate deeply within WordPress management by offering a comprehensive overview necessary for maintaining website performance, improving user experience, and ensuring security. They facilitate a seamless operating environment where each request type is mapped to its role in the ongoing monitoring and optimization of the WordPress platform.
Log Analysis
Analyzing WordPress access logs is a fundamental practice for enhancing the performance, security, and user experience of a WordPress website. These logs record crucial data such as IP addresses, timestamps, requested URLs, and status codes, each playing a pivotal role in the effective management of the site. Understanding access logs provides valuable insights that help in diagnosing issues, preventing security breaches, and optimizing resource usage.
Access logs capture a variety of data points that are instrumental in the comprehensive analysis of a website’s operational health. These typically include IP addresses, which indicate the origin of web traffic, timestamps that chronicle when visits occur, requested URLs that show the specific content accessed, and status codes that report the success or failure of these requests. Together, these elements form a robust dataset used for troubleshooting and performance reporting.
Log analysis methodologies often involve tools and practices that emphasize accuracy and efficiency. Techniques such as pattern detection and automated alerts can help in identifying unauthorized access attempts or unusual traffic spikes. These insights are not only crucial for preempting security threats but also form the basis for informed decisions on site improvements and scaling.
The effective analysis of log data leads to tangible enhancements in website security frameworks and user experience design. By regularly monitoring access logs, site administrators can identify trends, such as peak usage times, and adapt server resources accordingly to maintain optimal performance. Highlighting security breaches early enables timely interventions, thereby safeguarding user data and reducing vulnerabilities.
Overall, the consistent appraisal of WordPress access logs ensures that the site remains both robust and user-friendly, ultimately supporting the goals of the broader WordPress development framework. This practice solidifies the foundation for a secure, efficient, and responsive online presence.
Traffic Patterns
Understanding traffic patterns is essential for gaining insights into user interactions on a WordPress website. WordPress access logs stand as a central resource in tracking these patterns, offering invaluable data to enhance site performance. By examining these logs, one can analyze when users visit the site, which pathways they take, and how they engage with different pages. This log data not only records traffic but helps website administrators identify peak times of use, allowing for more strategic server management.
Access logs are a critical tool in analyzing traffic patterns, serving as a foundation for identifying potential capacity enhancements. Recognizing when the highest volumes of visitors access the site can guide decisions around scaling server resources and adjusting configurations to accommodate these spikes efficiently. Moreover, this data can pinpoint bottlenecks or pages that consistently experience high traffic and may benefit from performance optimization.
Traffic patterns derived from access logs can directly inform server configuration optimizations. By understanding the user flow, administrators can make informed decisions on caching strategies, load balancing, and other server adjustments to improve site speed. Additionally, these patterns contribute to enhanced user experiences by ensuring that the site remains responsive and functional during high traffic periods. Ultimately, leveraging traffic patterns through careful analysis of access logs facilitates a more robust and efficient WordPress website, improving user engagement and satisfaction while optimizing bandwidth usage.
Error Detection
Error Detection
In the realm of WordPress, understanding access logs is crucial for maintaining the health and security of your website. WordPress access logs are files that record server activity related to website visits and interactions. They provide a detailed account of every request made to your server, including the time, IP address, request type, and response status. These logs are indispensable when it comes to error detection, as they help identify patterns and anomalies that could indicate underlying issues affecting website performance.
Access logs play a pivotal role in troubleshooting WordPress sites. They allow you to pinpoint recurring errors, such as 404 or 500 errors, which may point to broken links or server misconfigurations. By analyzing these logs, you can uncover the root causes of these issues, enabling timely resolutions and enhancing your site’s reliability.
For WordPress developers and administrators, leveraging access logs involves several key steps. First, identify errors by reviewing log entries for unsuccessful HTTP requests or unexpected behavior. Next, utilize this data to interpret and address common issues. For instance, frequent 404 errors could suggest outdated links, requiring updates to your content or redirection rules.
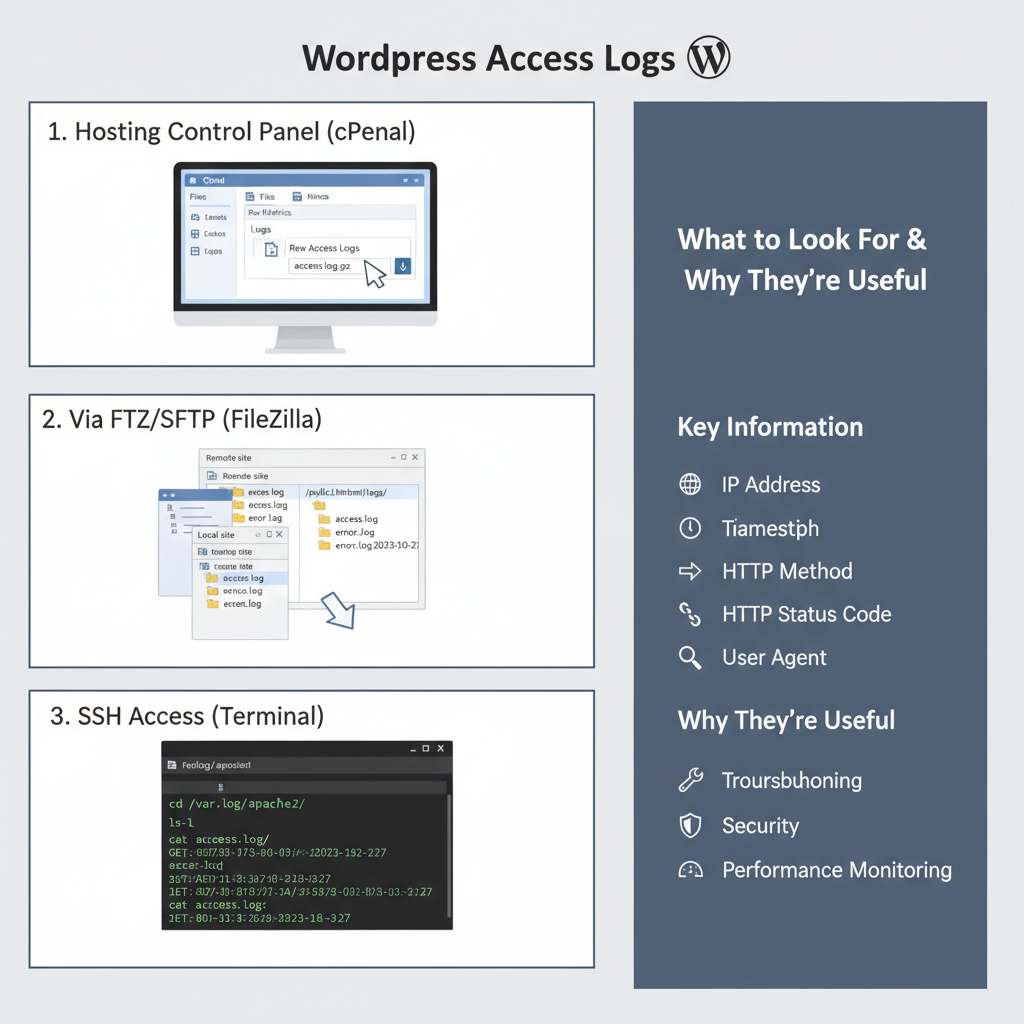
To effectively manage error detection via access logs, it’s essential to know how to access and interpret these records. Most hosting providers allow easy access through control panels or direct server access methods. Once accessed, use log analysis tools or software to parse and interpret the data for actionable insights.
Ultimately, the strategic use of WordPress access logs in error detection and troubleshooting fosters improved website maintenance practices. By routinely examining these logs, you can ensure that your WordPress site remains functional and secure, while also optimizing performance.
Security Monitoring
Security monitoring plays a pivotal role in safeguarding WordPress websites. It forms a crucial part of maintaining the integrity and reliability of a site by continuously observing for any potential threats or anomalies. Access logs are integral to this process, providing detailed records of who interacts with the website and how. By scrutinizing these logs, administrators can detect unexpected behaviors or unauthorized attempts to access sensitive information, enabling quick responses to potential security breaches.
Essential practices include real-time monitoring, where security plugins continuously scan for threats and toolbar intrusions. These tools operate using sophisticated algorithms to recognize patterns indicative of malicious activities, ensuring that any anomaly is flagged promptly. WordPress security plugins are equipped to handle this task efficiently, offering a variety of features, including firewall protections, malware scanning, and vulnerability assessments. They work by analyzing traffic, assessing for established risk factors, and adapting to evolving threats.
In addition to continuous monitoring, having a robust threat detection strategy is paramount. This involves setting up alerts for suspicious activities, such as repeated failed login attempts or unexpected bandwidth usage, as logged in the access data. By employing these strategies, website administrators can quickly address potential issues before they escalate, maintaining overall site health and user trust.
Ultimately, the collaborative use of access logs analysis and dedicated security tools creates a formidable defense against cyber threats. By embracing these security monitoring techniques, WordPress site owners can ensure their platform remains secure, resilient, and efficient in protecting sensitive user data. The emphasis is on not just identifying threats but fortifying the site’s security framework to prevent future vulnerabilities.
Log Management
Log management is a crucial element for effectively managing WordPress websites. Access logs, in particular, are vital records that document every request made to a server, providing insights into user interactions and potential security threats. These logs serve as a foundational tool for analyzing traffic patterns, identifying performance bottlenecks, and detecting unauthorized activities, thereby playing a pivotal role in optimizing a WordPress website’s performance and security.
WordPress access logs typically consist of various data points such as IP addresses, request types, and timestamps. These logs can detail which pages are being accessed, what methods are used for requests, and where the requests are coming from — all of which help in building a comprehensive picture of the website’s usage. The data collected can be invaluable for troubleshooting issues, making data-driven decisions for performance improvements, and implementing proactive monitoring strategies to safeguard the site against potential threats.
To manage these logs effectively, several tools and techniques are at a WordPress administrator’s disposal. Popular plugins and tools can automatically collect, filter, and analyze log data, enabling real-time monitoring and automated incident responses. These tools integrate seamlessly with existing WordPress installations, providing interfaces and dashboards that streamline log management operations. They offer features such as automated log retrieval and systematic storage, which further enhance the efficiency of website management.
The benefits of adept log management are manifold. By utilizing access log analysis, website administrators can implement performance optimization strategies that ensure a faster, more reliable user experience. Moreover, consistent monitoring and automated threat detection can significantly enhance security by identifying unusual patterns indicative of malicious activities. This proactive approach not only fortifies the website against attacks but also maintains the integrity of the website data.
In summary, effective log management is instrumental in improving the operational robustness of a WordPress website. By harnessing the power of detailed access logs, administrators can enhance website performance, ensure data integrity, and facilitate swift incident response. This leads to a more seamless user experience and a fortified security posture, underscoring the indispensable value of log management in the domain of WordPress development.