Within the complex landscape of WordPress development, the capability to require users to log in plays an integral part in defining a site’s operational efficacy and security. As a fundamental feature, the WordPress login protocol serves as a gatekeeper, managing access and facilitating personalized experiences while safeguarding the digital environment.
Requiring users to log into WordPress is not merely about restricting access; it’s a strategic component that amplifies site security. By establishing robust user authentication mechanisms, this functionality acts as a first line of defense against unauthorized access, ensuring that sensitive data and content are accessible only to verified identities. Moreover, login features empower site administrators with crucial capabilities for user management, allowing them to assign varying levels of access, from general viewers to contributing authors and administrators.
In addition to security, login requirements foster a tailored user experience. By collecting data through user interactions, WordPress sites can offer customized content and features that resonate with individual user preferences and behaviors. This personalization extends to content accessibility, ensuring that specific posts or features are reserved for registered members or subscribers, thereby enhancing the value provided to the user.
Technical implementation of these login protocols involves configuring WordPress settings precisely to define user roles and permissions, leveraging plugins for added security measures, and enabling features such as two-factor authentication. The meticulous configuration ensures the seamless operation of login processes, fostering an engaging and secure environment for both users and administrators.
Login capabilities also contribute to the broader narrative of data management and user engagement. By tracking user behavior, site administrators can glean insightful analytics that inform content strategies and enhance user satisfaction. The requirement for login thus serves not only as a protective measure but also as a tool for enhancing the interactive and operational aspects of a WordPress site.
Future discussions will delve deeper into the specific configurations and optimizations possible within WordPress to enhance these login features, reflecting the symbiotic relationship between security practices and effective WordPress site management.
User Authentication
The user authentication system plays a pivotal role in the realm of WordPress website development, serving as a crucial element in safeguarding both the site and its users. By establishing a robust login framework, WordPress developers ensure that only authorized individuals gain access to certain areas of a website, thereby fortifying the overall security architecture.
Implementing a reliable login process in a WordPress environment involves a series of strategic measures. At the core of this is the setting up of secure login pages, which often incorporates elements like SSL certificates to encrypt data during transmission, thereby shielding it from potential breaches. Additionally, these mechanisms often leverage two-factor authentication, an enhancement that requires users to provide a second form of verification beyond just a password. This method greatly reduces the risk of unauthorized access, providing an additional layer of security that is crucial for protecting sensitive information.
Moreover, in the context of user roles within WordPress, defining and managing distinct user permissions becomes an integral part of maintaining site integrity and functionality. By clearly demarcating user roles, site administrators can control who has access to modify content, manage plugins, or alter settings, ensuring operational consistency and precision.
Maintaining the dependability and efficacy of user authentication systems is not just about implementing security measures. It also involves a commitment to ongoing management and updates, which can entail regular password audits, user activity monitoring, and system upgrades. These practices help in detecting and deterring potential threats early, preserving the uninterrupted operation of the WordPress site.
In summary, user authentication within WordPress development is about more than just permitting access; it is about constructing a secure, manageable, and adaptable framework that aligns with the broader objectives of website security and user experience. This system safeguards the website’s assets, ensuring that user interactions are protected and that the site’s operations remain seamless and secure.
Login Security
In the realm of WordPress website management, login security emerges as a pivotal element in safeguarding both site integrity and user data. The requirement for users to log in is not merely a formality but a robust mechanism to enhance trust and data security. This essential security measure aligns with WordPress’s overarching commitment to secure web development, providing a fortified structure against potential cyber threats.
Ensuring login security in WordPress is integral to maintaining a trustworthy digital environment. By enforcing secure login protocols, WordPress significantly mitigates risks such as unauthorized access and data breaches. This protective layer includes various measures like enforcing strong password policies and implementing multi-factor authentication. Such policies require users to create complex, unpredictable passwords, thereby reducing vulnerability to brute force attacks. Multi-factor authentication adds an extra layer of security by necessitating a second form of verification, such as a biometric scan or a unique code sent to a mobile device.
The effectiveness of WordPress’s login security is further complemented by its ability to control login attempts, setting limits that prevent automated hacking tools from gaining unauthorized access. By requiring authenticated logins, WordPress ensures that only verified users can access sensitive areas of the website, thereby protecting user credentials and site data from malicious entities.
In creating secure user authentication processes, WordPress emphasizes the importance of encryption standards. These protect the data exchanged during the login process, ensuring that user information remains confidential. Such security measures are crucial in maintaining the platform’s reputation for reliability and integrity in web development.
Ultimately, the requirement for login security in WordPress is a testament to its dedication to fostering a secure and trustworthy environment. By implementing rigorous authentication and protection protocols, WordPress not only secures user data but also strengthens trust among its users, fortifying their overall interaction within the digital landscape.
Login Customization
In the realm of WordPress website development, enhancing the login process is crucial for both security and user experience. Customizing the login interface on a WordPress site plays a vital role in ensuring that users have a seamless and personalized experience when accessing the site. This approach not only bolsters security but also aligns with the user’s expectations for a modern digital interface.
One of the primary methods to achieve this is through the use of WordPress plugins specifically designed to modify login experiences. Plugins offer a variety of functionalities—from basic aesthetic changes to comprehensive security enhancements. For instance, developers can opt to integrate custom plugins that allow for a complete overhaul of the login page design, matching it with the site’s theme and branding. This visual continuity is key in providing a cohesive user experience.
Moreover, these customizations often include the implementation of advanced security features. Many WordPress plugins facilitate the addition of two-factor authentication, enforcing stronger login credentials and providing an extra layer of protection against unauthorized access. This integration is essential in maintaining high security standards, particularly for sites handling sensitive user data.
Besides security plugins, user role management tools are also pivotal. They enable developers to dictate specific access levels and permissions, ensuring users only have access to the parts of the site they need. This not only enhances security but also streamlines user navigation, as visitors interact with content pertinent to their roles.
Technical and visual modifications work in tandem in WordPress login customization. On the technical side, alterations to login scripts can enhance performance and security. Visually, a well-designed login interface can provide an inviting point of entry for users, reflecting the professionalism and reliability of the brand.
Ultimately, the pursuit of login customization must balance functionality with aesthetics, aiming to improve both usability and protection concurrently. By doing so, developers ensure their WordPress websites are not only secure but also welcoming environments that adhere to modern web standards, creating a robust overall experience for every user.
Custom Login URLs
Custom login URLs in WordPress are a crucial aspect of managing user access and enhancing security on your site. By modifying these URLs, WordPress provides an opportunity to refine how users interact with your login process, focusing on safeguarding the site while customizing the user experience.
When evaluating the necessity for custom login URLs, it’s imperative to understand their role in controlling access points to your site. Standard WordPress installations use predictable login paths, which present vulnerabilities to unauthorized access and brute force attacks. Customizing these paths mitigates such risks by making the login endpoints less obvious to potential intruders, thereby bolstering site security.
Implementing custom login URLs is a strategic move that aligns with broader WordPress development practices. The initial step involves renaming the login endpoint using a plugin or coding adjustments in your site’s functions file. This alteration serves dual purposes: disrupting automated attack patterns and optimizing the login workflow to suit bespoke user journeys. Custom URLs can reroute users post-login, adding another layer of personalization and directing them to relevant areas of the site, further enhancing the user experience.
Moreover, addressing potential challenges in customizing login URLs involves a careful balance between security configurations and user accessibility. Ensuring that users are adequately informed about URL changes keeps login processes smooth and minimizes confusion. Anticipating compatibility issues with plugins is also crucial, as not all plugins may support custom login paths. Regular testing and updates are necessary to maintain the integrity of login functionalities.
Overall, custom login URLs support the overarching theme of requiring logins in WordPress. They embody a fusion of security enhancements and user-centric design, ultimately contributing to a fortified and flexible WordPress environment. This approach epitomizes the essential attributes of user authentication and access control, intrinsic elements that secure the site and define user interaction pathways.
Login Redirects
Login redirects are an essential part of managing a WordPress website, especially in the context of site development and security. In WordPress, login redirects serve as a mechanism to direct users to specific pages immediately after they log in. This functionality is crucial for enhancing both the security and user experience of a WordPress website.
A login redirect ensures that users are automatically taken to a predefined location, such as a member dashboard or a customized landing page, rather than the default WordPress admin area or a generic homepage. This helps manage user workflows more effectively by guiding them to relevant areas of the site instantly, which can be particularly beneficial for websites with multiple user roles and permissions.
Implementing login redirects can be achieved through WordPress core capabilities by adding code snippets to a theme’s functions.php file or by utilizing plugins designed to manage redirects easily without coding. The simplicity of implementing such redirects through plugins makes it accessible even to those with minimal technical knowledge. Plugins often provide a straightforward interface, empowering site administrators to configure redirects for various user roles and conditions, thus optimizing user flow and site management.
Beyond improving workflow, login redirects significantly enhance website security. By redirecting users away from standard admin URLs, these redirects can obscure and protect sensitive areas from potential unauthorized access. This functionality decreases the risk of brute force attacks targeting the WordPress admin panel by making it less predictable.
Common challenges with implementing login redirects include compatibility issues with certain plugins or themes, which can sometimes interfere with the redirect logic. Solutions typically involve testing in staging environments and ensuring all elements are up to date before applying changes to the live site. Additionally, careful planning of user flow and role-specific redirects helps avoid confusion and ensures a seamless experience for all users.
In essence, login redirects are a vital component of WordPress site management, offering significant advantages in terms of security and user experience when properly configured. They are a testimony to the customizable nature of WordPress, allowing administrators and developers to tailor the website to meet precise user needs.
User Roles
In the WordPress environment, user roles are pivotal in ensuring efficient website management and security. Each role—Administrator, Editor, Author, Contributor, Subscriber, and Custom User Roles—comes with unique permissions and responsibilities that contribute to the overall functionality of a WordPress website.
The Administrator Role serves as the backbone of website management, holding the most power. This role encompasses complete control over all aspects of the site, from installing plugins to managing users. This comprehensive access ensures seamless integration of changes, crucial for maintaining a secure and updated website environment.
The Editor Role focuses on content management. Editors have the rights to publish, edit, and delete any posts or pages, making them critical for maintaining website content quality and consistency. Their ability to manage categories and tags further enhances the site’s organizational structure, directly impacting user experience.
Authors, by contrast, are limited to their own content. They can write, edit, and publish their posts, giving them autonomy in content creation while maintaining overall site integrity through restricted access. This distinction is vital for websites with multiple contributors, allowing for diversified content without compromising site security.
Contributors can draft posts but cannot publish. They rely on Editors or Administrators to review and publish their content. This role enforces a higher level of content scrutiny, ensuring quality control before publication while encouraging community contributions.
The Subscriber Role is primarily focused on interaction with the website content in a customized way. Subscribers have no authority to create or modify content, reflecting their role as the audience. This limitation underscores the commitment to protecting the site’s content from unintended alterations.
Custom User Roles allow for tailored permissions that can adapt to specific site requirements. By defining unique roles based on specific needs, site administrators can fine-tune the capabilities of each user, enhancing operational efficiency and safeguarding the site from potential vulnerabilities.
Each of these roles plays a crucial part in forming a collaborative yet secure ecosystem within a WordPress website. By maintaining a structured hierarchy of permissions and responsibilities, user roles not only facilitate efficient content management but also reinforce the site’s protective measures, ensuring robust performance and an optimal user experience.
Role-Based Access
Role-Based Access is a central aspect of managing permissions and access control within WordPress. It governs how different users interact with a website, defining what they can see and do based on their specific roles. Understanding and implementing Role-Based Access is crucial for maintaining security and optimizing user management on a WordPress platform.
In a WordPress environment, the concept of user roles is integral to web security and effective content management. User roles dictate specific permissions, restricting or permitting access to various parts of a website’s dashboard and content. This structured approach is essential for safeguarding sensitive information and ensuring that each user has the appropriate level of access according to their role.
Implementing Role-Based Access in WordPress involves assigning each user a role with predefined capabilities. These roles include Administrator, Editor, Author, Contributor, and Subscriber, each with a unique set of permissions. For instance, while an Administrator has complete control over all site functionalities, a Contributor can only draft posts. This hierarchical structure not only enhances security by preventing unauthorized access but also facilitates efficient content management by delineating responsibilities.
Moreover, Role-Based Access is dynamic, allowing changes in user capabilities as needed. This flexibility is vital for adapting to evolving security needs and enhancing user interaction based on emerging requirements. As such, Role-Based Access not only secures content but also empowers user engagement by allocating the right tools and permissions for each role.
Strategically, implementing Role-Based Access in WordPress ensures a robust governance structure. It facilitates clear pathways for content approval processes, thereby reducing errors and improving workflow efficiency. Technically, it involves configuring settings to match role-specific requirements, thereby enhancing site performance and reliability.
By effectively managing roles and permissions, WordPress administrators can ensure that their site not only functions optimally but also aligns with security best practices. Each role is assigned precise permissions, thus mitigating risks associated with unauthorized access and enhancing the user experience by enabling seamless navigation across the site.
In conclusion, Role-Based Access is a cornerstone of secure and efficient WordPress site management. It strategically balances access control with user empowerment, ensuring that the site operates smoothly while safeguarding critical information. This system underpins both the strategic and technical facets of WordPress development, making it indispensable for any robust digital platform.
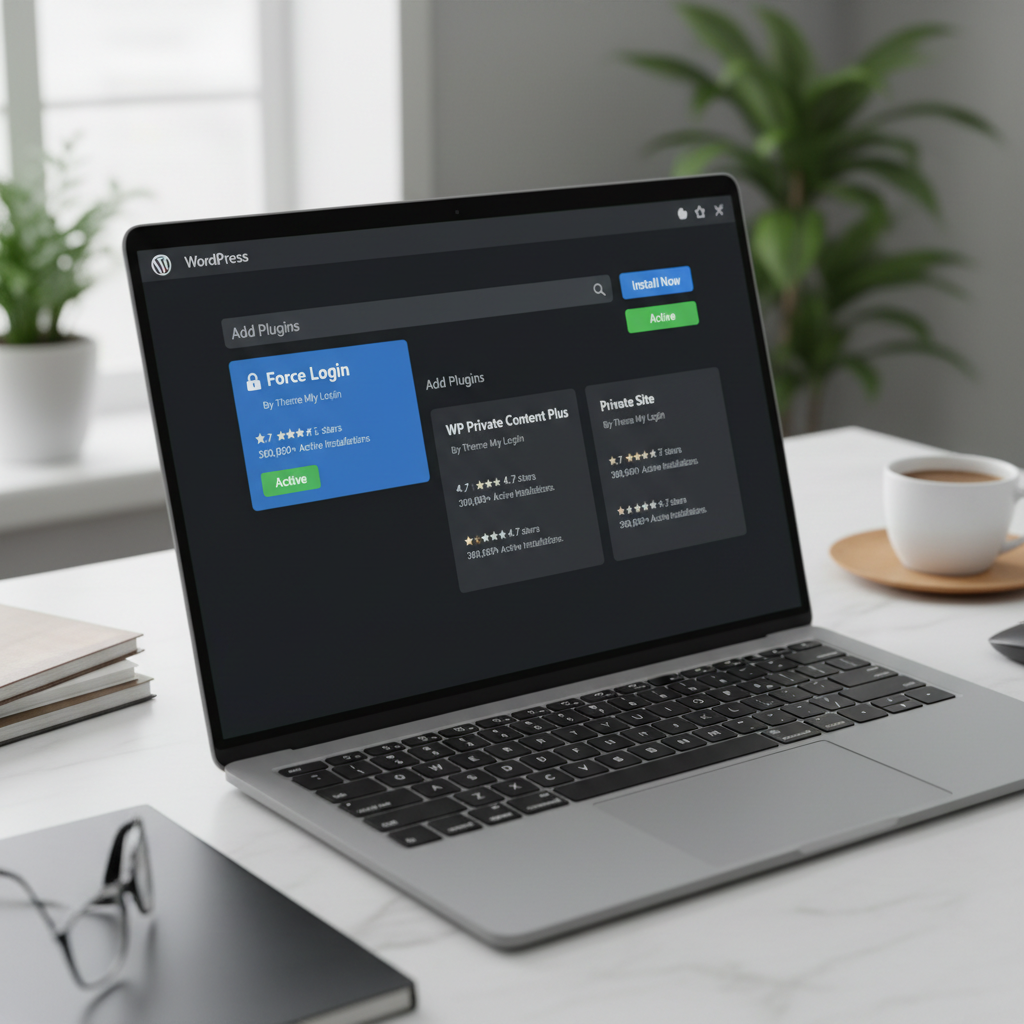
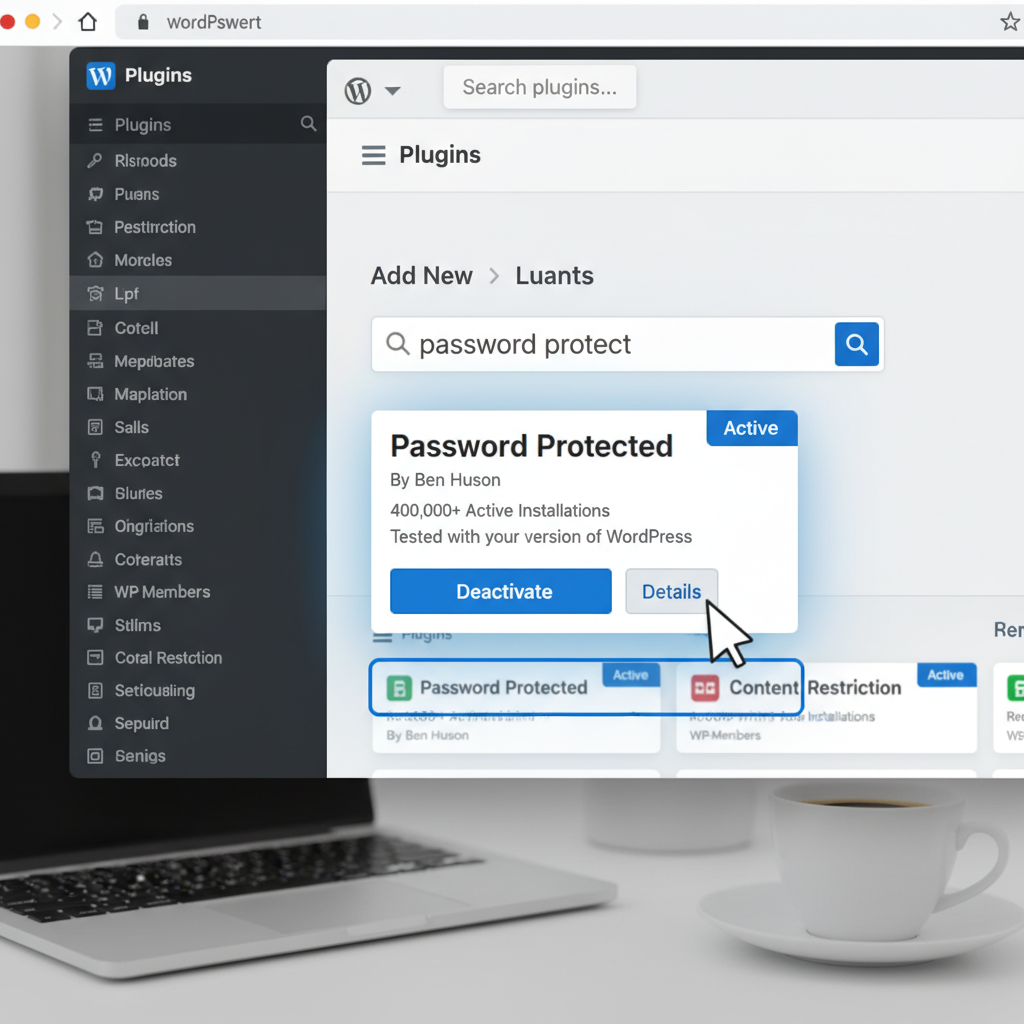
Login Plugins
On a WordPress website, login plugins are crucial components that play a significant role in enabling user authentication while enhancing both security and user experience. These plugins secure access by requiring users to authenticate, thus serving as a gatekeeper to the website’s content. By managing login protocols, these plugins protect user data, providing a safer environment for interactions within the WordPress site.
Login plugins execute a variety of functions tailored to improve security and engagement. They integrate seamlessly with WordPress to control access, applying security measures like two-factor authentication. This feature adds an extra layer of security by requiring users to confirm their identity through a secondary device or application, significantly reducing unauthorized access attempts. Additionally, plugins offering social login capabilities streamline the user experience by allowing users to log in through pre-existing social media accounts, enhancing convenience without compromising security.
By utilizing user role management features, these plugins help site administrators customize access permissions, ensuring that users have access only to areas relevant to their needs. Such user role management strengthens internal security protocols by preventing unauthorized changes or access to sensitive data.
Furthermore, these plugins can be efficiently integrated with other WordPress features to create a cohesive security framework that benefits both the site and its users. Advanced plugins offer detailed customization options, allowing administrators to design personalized login pages that align with the website’s branding and functionality needs.
Overall, the deployment of these plugins results in enhanced security infrastructure and improved user engagement and satisfaction, revealing their indispensable role within the WordPress ecosystem. These plugins not only safeguard the site but also contribute to a streamlined, user-friendly interface that supports both community building and robust security measures.
Popular Plugins
In the realm of managing user access for a WordPress website, plugins serve as essential tools to ensure effective login procedures and enhance security. WordPress plugins are indispensable for website developers seeking to manage user authentication and improve overall site functionality. As the backbone of user access management, these plugins offer solutions for various aspects of login authentication, playing a crucial role in both the security and the user experience.
Security enhancement plugins are pivotal in fortifying the login process against unauthorized access. By integrating advanced security protocols, these plugins protect websites from malicious attempts, safeguarding sensitive user data. They often include features such as two-factor authentication, which adds an extra layer of security, ensuring that only authorized users gain access to the site.
Plugins designed for user role management further complement the login procedure by allowing administrators to define and manage user permissions efficiently. This ensures that each user has access only to the specific areas necessary for their role, maintaining a structured and secure environment within the website.
The installation process of these plugins is typically straightforward, allowing even novice users to easily configure settings tailored to their needs. The configuration step is crucial, as it aligns the plugin functionalities with the unique requirements of each WordPress site, ensuring optimized performance and user satisfaction.
Through a cohesive integration of these plugins, WordPress facilitates a robust ecosystem for managing user access effectively. This not only enhances security but also contributes to a seamless user experience, ultimately supporting the larger narrative of comprehensive WordPress website development. By carefully selecting and implementing these plugins, website administrators can achieve a balanced approach to access management, reinforcing the WordPress site’s overall integrity and trustworthiness.